- First open terminal. We need to know the name of the wireless adapter connected to the computer.
- Thanks for the A2A. Short answer is that you cannot. Long answer: The mac terminal app is just a GUI interface to communicate with the internal shell i.e. Bash/unix shell. So on it’s own no shell has a wireless stack associated with it.
- Guys in this tutorial I am going to show you how to get password of saved wifi iilike my video stay updated by subscribing this.
Ever thought about getting INFINITE free WiFi at a Hotel, Cruise, Airport or ANYTHING ELSE? Well, me too, and today I'm going to show YOU HOW!
After the long holiday, first I want to say Merry Christmas and Happy new year 2014 to you. Today we will learn about 5 Steps Wifi Hacking – Cracking WPA2 Password. A lot of readers send many request regarding how to crack wireless WPA2 password in our request tutorial page.
According to Wikipedia :
Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access II (WPA2) are two security protocols and security certification programs developed by the Wi-Fi Alliance to secure wireless computer networks. The Alliance defined these in response to serious weaknesses researchers had found in the previous system, WEP (Wired Equivalent Privacy)
A flaw in a feature added to Wi-Fi, called Wi-Fi Protected Setup (WPS), allows WPA and WPA2 security to be bypassed and effectively broken in many situations. Many access point they have a Wifi Protected Setup enabled by default (even after we hard reset the access point).
Requirements:
1. Wireless card (support promiscuous mode)
In this tutorial I use ALFA AWUS036H from Amazon.
2. Access point with WPA2 and WPS enables
5 Steps Wifi Hacking – Cracking WPA2 Password:
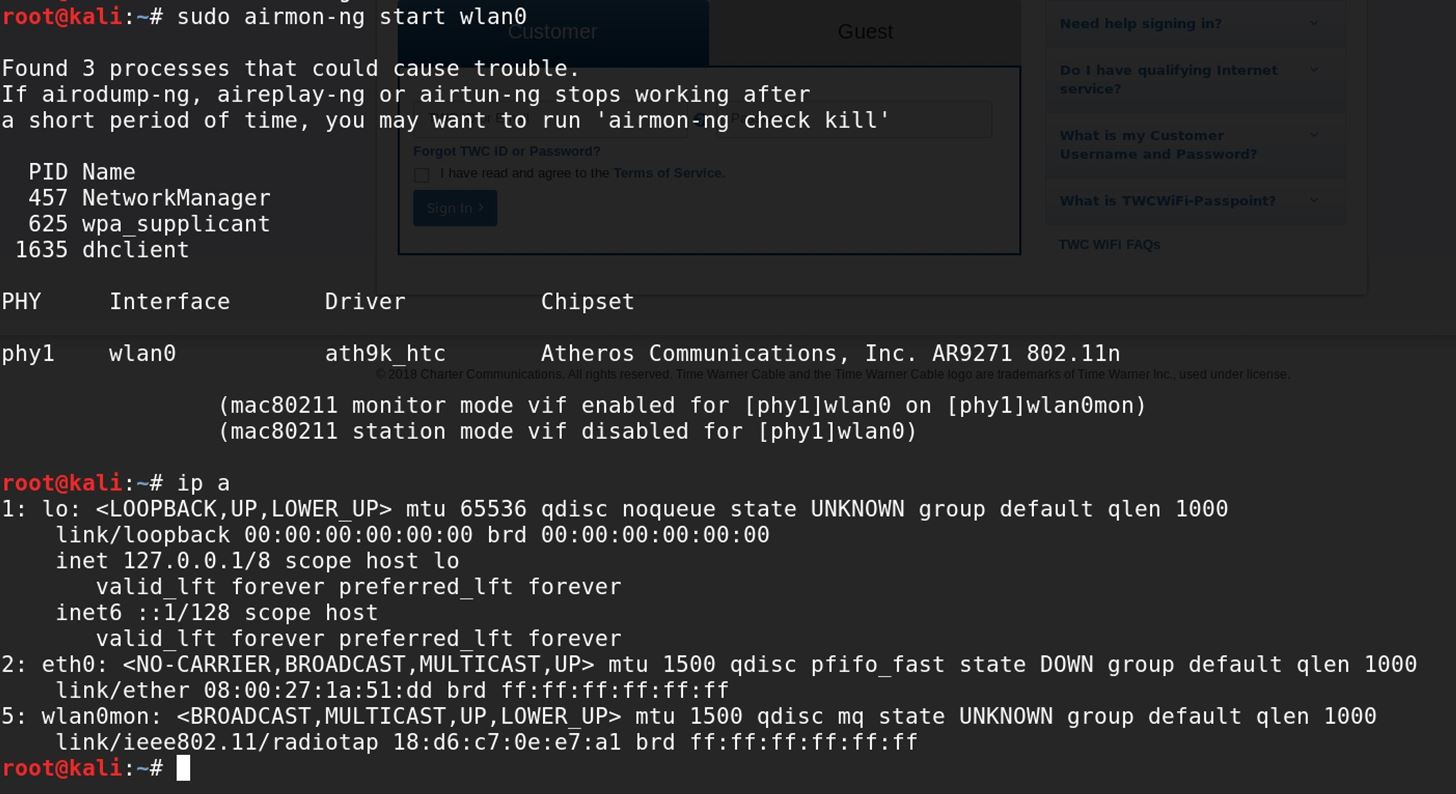
1. Open our terminal (CTRL+ALT+T) and type airmon-ng (view tips and tricks how to create keyboard shortcut on kali linux)
this command will lists our wireless card that attached with our system.
2. The next step we need to stop our wireless monitor mode by running airmon-ng stop wlan0
3. Now we ready to capture the wireless traffic around us. By running airodump-ng wlan0 our wireless interface will start capturing the data.
From the picture above, we can see many available access point with all the information. In the green box is our victim access point which is my own access point 🙂
Information:
BSSID (Basic Service Set Identification): the MAC address of access point
PWR: Signal level reported by the card.
Beacons: Number of announcements packets sent by the AP
#Data: Number of captured data packets (if WEP, unique IV count), including data broadcast packets.
#/s: Number of data packets per second measure over the last 10 seconds.
CH: Channel number (taken from beacon packets).
MB: Maximum speed supported by the AP. If MB = 11, it’s 802.11b, if MB = 22 it’s 802.11b+ and higher rates are 802.11g.
ENC: Encryption algorithm in use.
CIPHER: The cipher detected. TKIP is typically used with WPA and CCMP is typically used with WPA2.
AUTH: The authentication protocol used.
ESSID: Shows the wireless network name. The so-called “SSID”, which can be empty if SSID hiding is activated.
4. From the step 3 above, we can find access point with encryption algorithm WPA2 and note the AP channel number. Now we will find out whether target AP has WPS enabled or not.
wash -i wlan0 -c 8 -C -s
if the WPS Locked status is No, then we ready to crack and move to step 5.
5. The last step is cracking the WPA2 password using reaver.
reaver -i <your_interface> -b <wi-fi victim MAC address> –fail-wait=360
Because we already get the information from step 3 above, so my command look like this:
reaver -i wlan0 -b E0:05:C5:5A:26:94 –fail-wait=360
it took about 5 hours to crack 19 characters WPA2 password (vishnuvalentino.com) from my Kali virtualBox, but it depend with our hardware and wireless card.
Conclusions:
1. WPA and WPA2 security implemented without using the Wi-Fi Protected Setup (WPS) feature are unaffected by the security vulnerability.
2. To prevent this attack, just turn off our WPS/QSS feature on our access point. See picture below (I only have the Chinese version 😛 )
Notes: Only practice this tutorial on your own lab and your own device. Hacking can be a crime if you don’t know where to put it.
Share this article if you found it was useful:
Blogger at hacking-tutorial.com. Love PHP, offensive security and web. Contact him at me[-at-]vishnuvalentino.com
See all posts by Vishnu Valentino || Visit Website : http://www.vishnuvalentino.com
DISCLAIMER: This article is for educational purposes only. This article should not be used for illegal activity. The author is not responsible for its use.
You are 18 and bored at your grandma’s place, there is no source of entertainment, but you find out there is a sweet wifi spot at your neighbours. You have gone through a lot of wifi cracking articles/videos but the more you try, the more frustrated you get to have it working correctly. I feel ya! Here’s where this article comes in handy.
Even though majority classify cracking wifi passwords for the professional’s, but this article is also targeted towards beginners who have very little knowledge on computers. So, feel free to give it a shot!
- You need to be familiar with the command line. Or at least, how to paste the commands on the terminal ;)
- You are using a Mac (or running OSX)
I am using a MacBook Pro (13-inch, 2017) running macOS High Sierra version 10.13.5. You can find yours by selecting the Apple icon on the menu bar (top left of your screen) and select About This Mac.
Lets create a folder on Desktop where we want to place all our work files in. You can change to your desired directory if needed.
Open the terminal (Command + Space and type Terminal). Once open, run the following commands
The my-wifi-cracking-work folder is now visible on your desktop screen.
Here’s how we plan to accomplish it:
- We first identifying the target network to crack
- Attempt to capture a 4 way handshake with our target network
- Finally, crack the network password!
Identifying the the target network #
Luckily OSX comes with wireless diagnostic tools that help with scanning/sniffing/etc. To access it, click on the wifi icon on the the menu bar while holding down the option key.
A dropdown menu will appear. Click on Open Wireless Diagnostics ....
Wireless Diagnostics window appears now, but we will not use the one shown. Click on Window on the menu bar and select Scan.
Note down the target networks channel and width.
Here’s an example of my target network:
Capturing 4-way handshake with your target network #
With the Wireless Diagnostics window open, click on Window on the menu bar and select Sniffer. Here, select the channel and width found from the previous step and press Start. The tool automatically tries to capture a handshake with the desired network, no prompt will be shown though.
Wait for 2-3 mins (we assume that is the typical time for a handshake to occur) and then press Stop.
On pressing Stop, the pcap file will be created on /var/tmp folder.
Lets now move this file into our work folder.
We need to convert the .pcap file to .hccapx file by uploading it here. If the handshake was captured in the file, this start the download of the .hccapx file. If not, you will need to try a bit longer than earlier stated to generate this file.
Downloadnaive-hashcat and extract into the work directory.
OR
Hack Wifi Password Using Mac Terminal Free
git clone it.
Then …
The cracking will take sometime depending on your hardware. To check your progress, you can press s where it would display an output similar to this:
Once done, the results will be storied in cracked.pot file. It will be in a format will be network name and password seperated by :
In this case the password is veryhardpassword123.
Hack Wifi Password For Pc
This article was inspired by the work of @brannondorsey and Lewis Encarnacion’s awesome tutorial